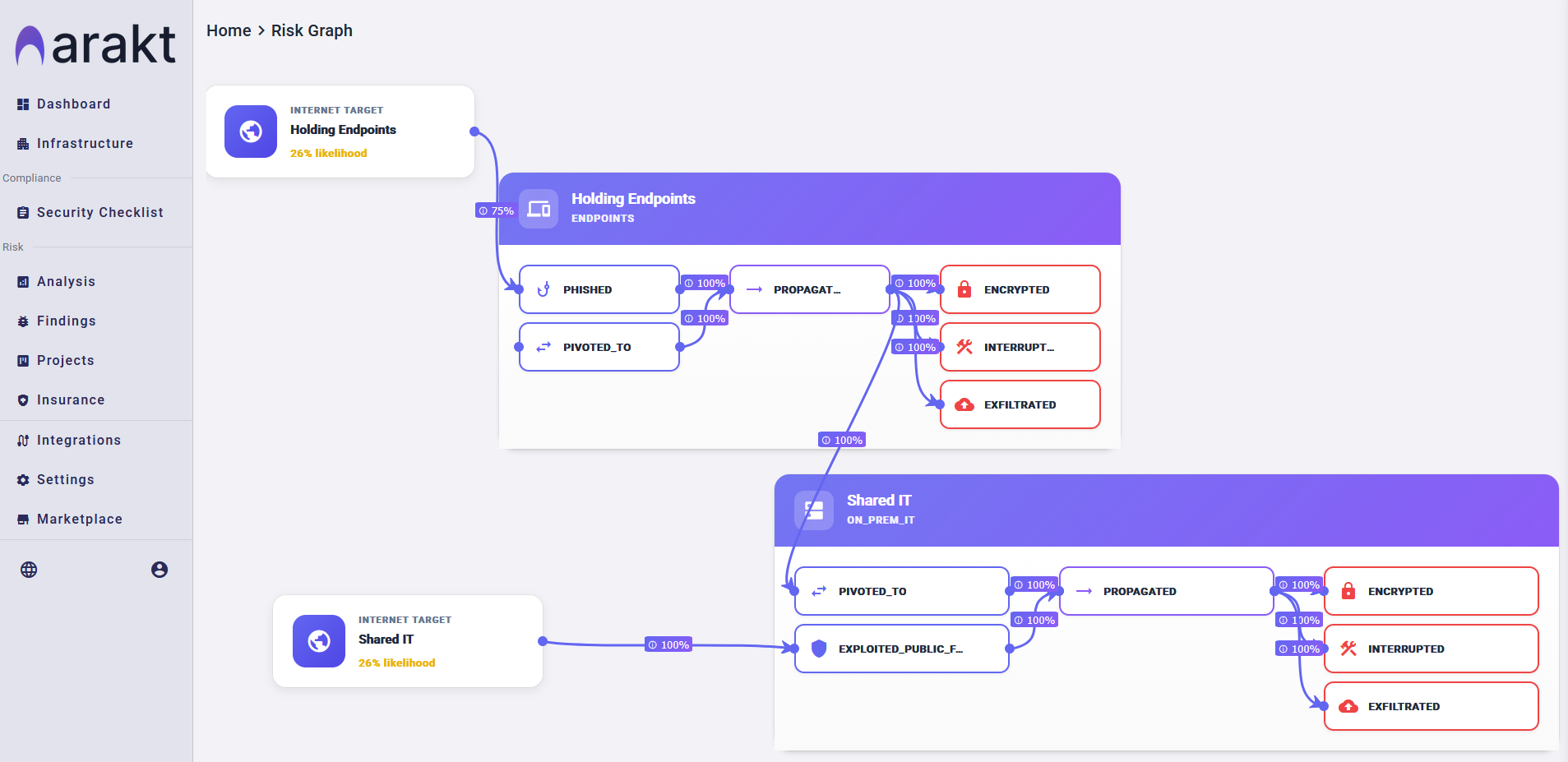
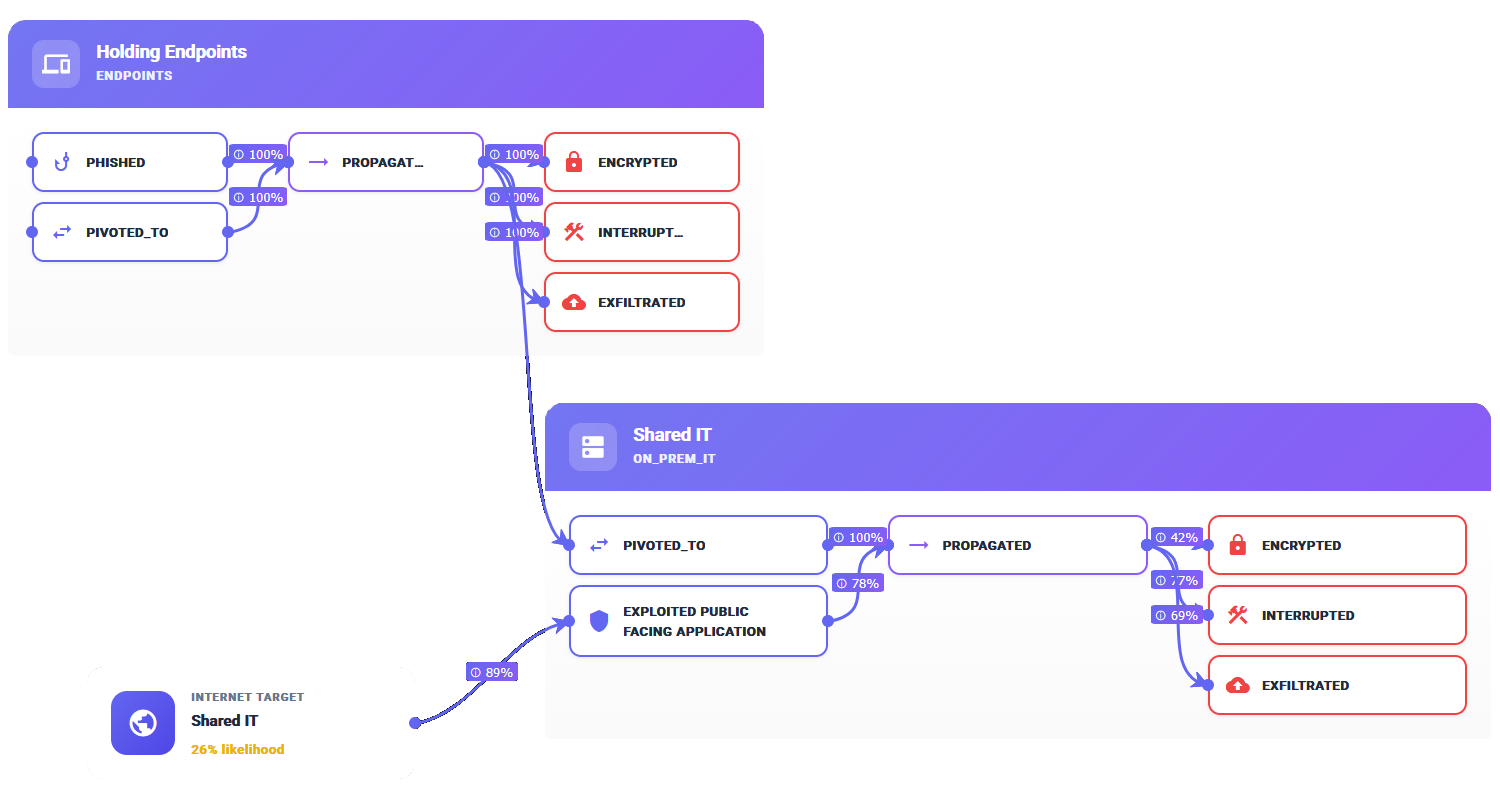
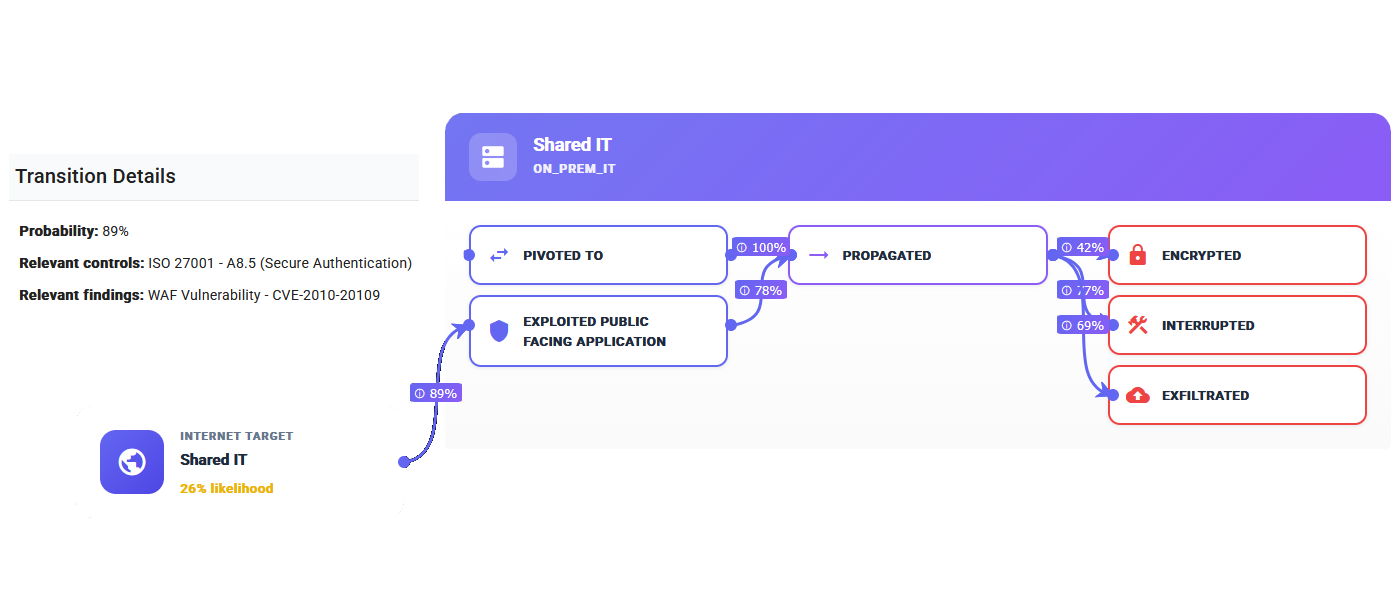
Map Cyber Risk Propagation Across Your Enterprise
Leverage sophisticated attack simulations to precisely discover potential lateral movement paths and meticulously map the propagation of cyber risk across your entire digital infrastructure with unparalleled accuracy.
Get a Demo